Today, I noticed two fresh vulnerabilities on the VBR12.1 Manager and console servers. Certain .net core requirements are installed when the product is installed. Unfortunately, The .net isn’t patched automatically through Windows updates.
CVE-2023-36049–.NET, .NET Framework, and Visual Studio Elevation of Privilege Vulnerability
https://msrc.microsoft.com/update-guide/vulnerability/CVE-2023-36049
Microsoft is releasing this security advisory to inform users of a vulnerability in .NET 6.0, .NET 7.0, and .NET 8.0 RC2. Additionally, this alert offers suggestions on how developers should update their apps to fix this vulnerability.
When untrusted URIs are sent to System .Net, a vulnerability in .NET allows for the elevation of privilege. It is possible to insert arbitrary commands into backend FTP servers using WebRequest.Create.
CVE-2023-36558–ASP.NET Core – Security Feature Bypass Vulnerability
https://msrc.microsoft.com/update-guide/vulnerability/CVE-2023-36558
Microsoft provides this security advisory to notify users about a vulnerability in ASP.NET Core 6.0, 7.0, and 8.0 RC2. Additionally, this alert offers suggestions on how developers should update their apps to fix this vulnerability.
An ASP.NET security feature bypass vulnerability allows an unauthorized user to circumvent validation on Blazor server forms, potentially leading to unwanted behaviours.
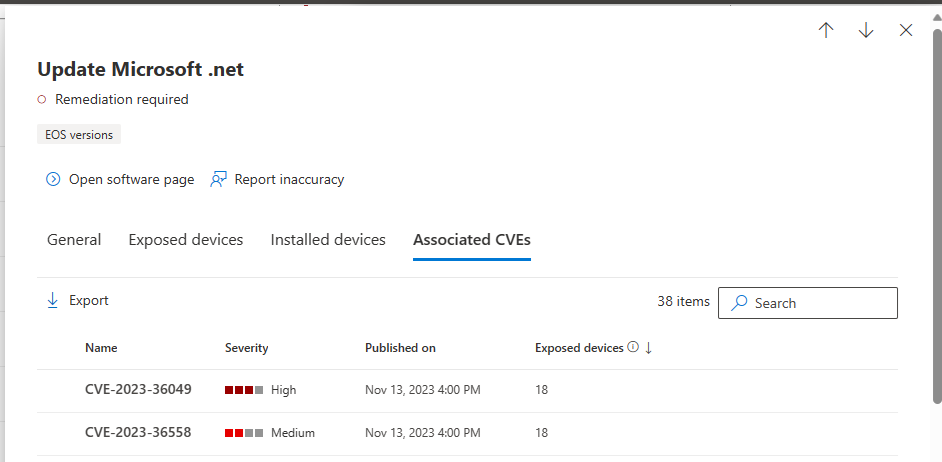
Affected software:
Any ASP.NET Core Blazor 6.0 application running on .NET 6.0.24 or earlier.
Any ASP.NET Core Blazor 7.0 application running on .NET 7.0.13 or earlier.
Any ASP.NET Core Blazor 8.0 application running on .NET 8.0 RC2.
Follow the steps below to fix the VBR 12.1 CVE-2023-36558 and CVE-2023-36049 vulnerabilities.
Please backup the server before making any changes.
1. Login to the Veeam servers.
2. Open Command Prompt as administrator.
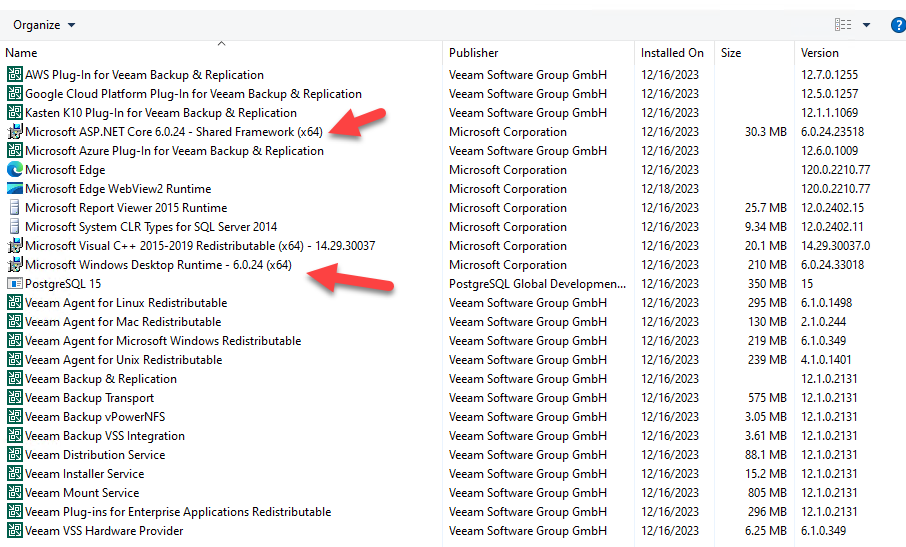
3. Programs and Features to check the .net version. The VBR 12.1 manager and console server install .net version 6.0.24 through the VeeamBackup&Replication_12.1.0.2131_20231206 iso image.
4.
Microsoft recommends downloading and installing patched version 6.0.25 and uninstalling the end of support .net version.
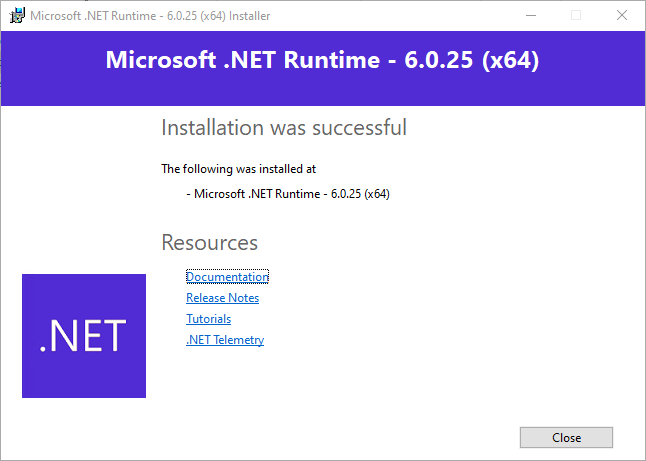
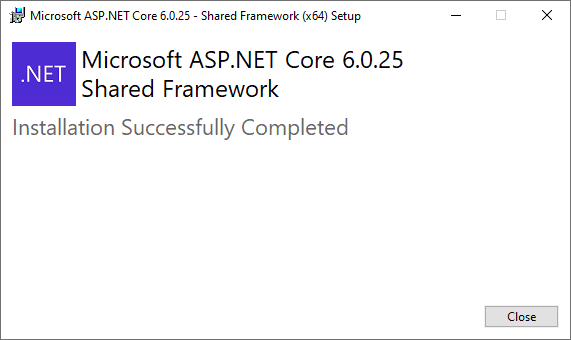
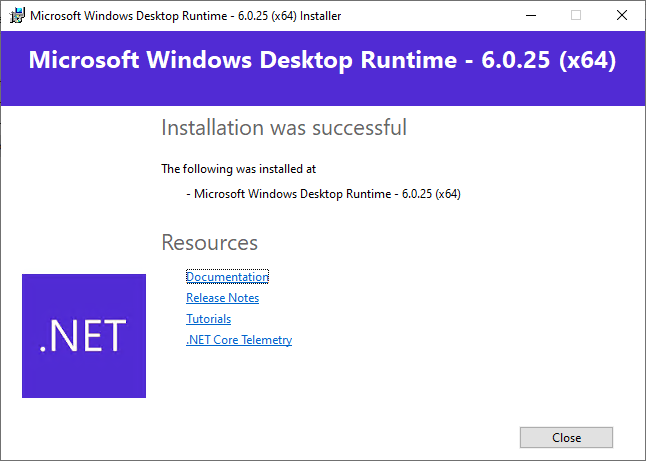
5. Programs and Features to check the .net version. You will see all of the .net version 6.0.25 installed.
6. Restart server.
Everything is fine so far, and the .net versions are patched.
I hope you enjoy this post.
Cary Sun
X: @SifuSun
Web Site: carysun.com
Blog Site: checkyourlogs.net
Blog Site: gooddealmart.com
Amazon Author: https://Amazon.com/author/carysun
